Configuring Snowflake PrivateLink
The PrivateLink feature is available on the following dbt Cloud Enterprise tiers:
- Business Critical
- Virtual Private
To learn more about these tiers, contact us at sales@getdbt.com.
The following steps walk you through the setup of a Snowflake AWS PrivateLink or Azure Private Link endpoint in a dbt Cloud multi-tenant environment.
PrivateLink endpoints can't connect across cloud providers. For a PrivateLink connection to work, both dbt Cloud and the server (like Snowflake) must be hosted on the same cloud provider. For example, AWS PrivateLink can’t connect to resources hosted on Azure, and Azure PrivateLink can’t connect to resources hosted on AWS.
Users connecting to Snowflake using SSO over a PrivateLink connection from dbt Cloud will also require access to a PrivateLink endpoint from their local workstation.
Currently, for any given Snowflake account, SSO works with only one account URL at a time: either the public account URL or the URL associated with the private connectivity service.
About private connectivity for Snowflake
dbt Cloud supports private connectivity for Snowflake using one of the following services:
- AWS PrivateLink
- Azure Private Link
Configure AWS PrivateLink
To configure Snowflake instances hosted on AWS for PrivateLink:
- Open a support case with Snowflake to allow access from the dbt Cloud AWS or Entra ID account.
- Snowflake prefers that the account owner opens the support case directly rather than dbt Labs acting on their behalf. For more information, refer to Snowflake's knowledge base article.
- Provide them with your dbt Cloud account ID along with any other information requested in the article.
- AWS account ID:
346425330055— NOTE: This account ID only applies to AWS dbt Cloud multi-tenant environments. For AWS Virtual Private/Single-Tenant account IDs, please contact Support.
- AWS account ID:
- You will need to have
ACCOUNTADMINaccess to the Snowflake instance to submit a Support request.
-
After Snowflake has granted the requested access, run the Snowflake system function SYSTEM$GET_PRIVATELINK_CONFIG and copy the output.
-
Add the required information to the following template and submit your request to dbt Support:
Subject: New Multi-Tenant (Azure or AWS) PrivateLink Request
- Type: Snowflake
- SYSTEM$GET_PRIVATELINK_CONFIG output:
- *Use privatelink-account-url or regionless-privatelink-account-url?:
- dbt Cloud multi-tenant environment
- AWS: US, EMEA, or AU
- Azure: EMEA only
*By default dbt Cloud will be configured to use privatelink-account-url from the provided SYSTEM$GET_PRIVATELINK_CONFIG as the PrivateLink endpoint. Upon request, regionless-privatelink-account-url can be used instead.
dbt Labs will work on your behalf to complete the PrivateLink setup. Please allow 3-5 business days for this process to complete. Support will contact you when the endpoint is available.
Configure Azure Private Link
To configure Snowflake instances hosted on Azure for Private Link:
- In your Snowflake account, run the following SQL statements and copy the output:
USE ROLE ACCOUNTADMIN;
SYSTEM$GET_PRIVATELINK_CONFIG;
- Add the required information to the following template and submit your request to dbt Support:
Subject: New Multi-Tenant (Azure or AWS) PrivateLink Request
- Type: Snowflake
- The output from SYSTEM$GET_PRIVATELINK_CONFIG:
- Include the privatelink-pls-id
- dbt Cloud Azure multi-tenant environment:
- dbt Support will provide the
private endpoint resource_idof ourprivate_endpointand theCIDRrange for you to complete the PrivateLink configuration by contacting the Snowflake Support team.
Create Connection in dbt Cloud
Once dbt Cloud support completes the configuration, you can start creating new connections using PrivateLink.
- Navigate to Settings → Create new project → select Snowflake.
- You will see two radio buttons: Public and Private. Select Private.
- Select the private endpoint from the dropdown (this will automatically populate the hostname/account field).
- Configure the remaining data platform details.
- Test your connection and save it.
Enable the connection in Snowflake
To complete the setup, follow the remaining steps from the Snowflake setup guides. The instructions vary based on the platform:
There are some nuances for each connection and you will need a Snowflake administrator. As the Snowflake administrator, call the SYSTEM$AUTHORIZE_STAGE_PRIVATELINK_ACCESS function using the privateEndpointResourceID value as the function argument. This authorizes access to the Snowflake internal stage through the private endpoint.
USE ROLE ACCOUNTADMIN;
-- AWS PrivateLink
SELECT SYSTEMS$AUTHORIZE_STATE_PRIVATELINK_ACCESS ( `AWS VPC ID` );
-- Azure Private Link
SELECT SYSTEMS$AUTHORIZE_STATE_PRIVATELINK_ACCESS ( `AZURE PRIVATE ENDPOINT RESOURCE ID` );
Configuring Network Policies
If your organization uses Snowflake Network Policies to restrict access to your Snowflake account, you will need to add a network rule for dbt Cloud.
You can request the VPCE ID from dbt Cloud Support, that you can use to create a network policy.
Using the UI
Open the Snowflake UI and take the following steps:
- Go to the Security tab.
- Click on Network Rules.
- Click on Add Rule.
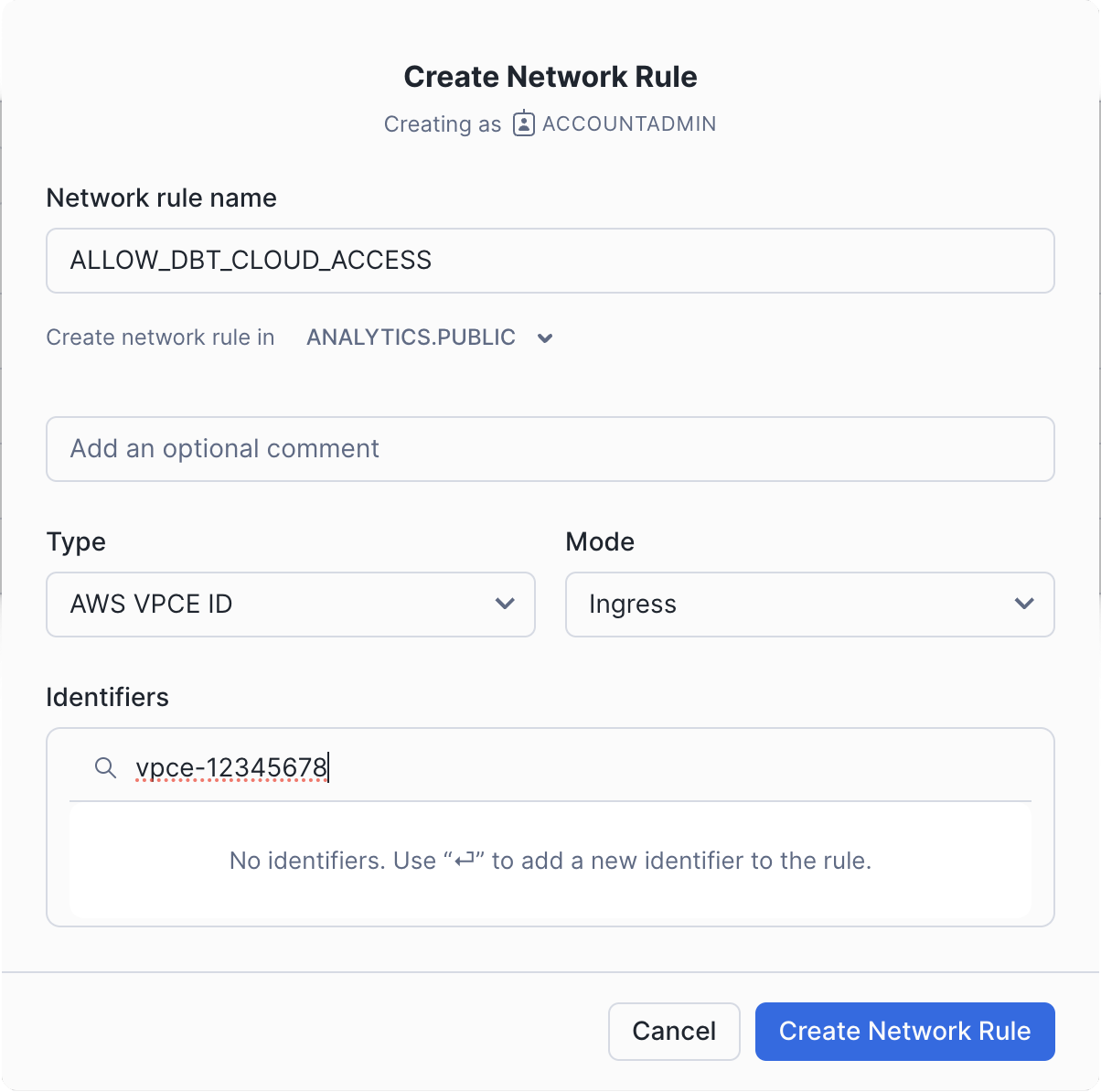
- Give the rule a name.
- Select a database and schema where the rule will be stored. These selections are for permission settings and organizational purposes; they do not affect the rule itself.
- Set the type to
AWS VPCE IDand the mode toIngress. - Type the VPCE ID provided by dbt Cloud Support into the identifier box and press Enter.
- Click Create Network Rule.
-
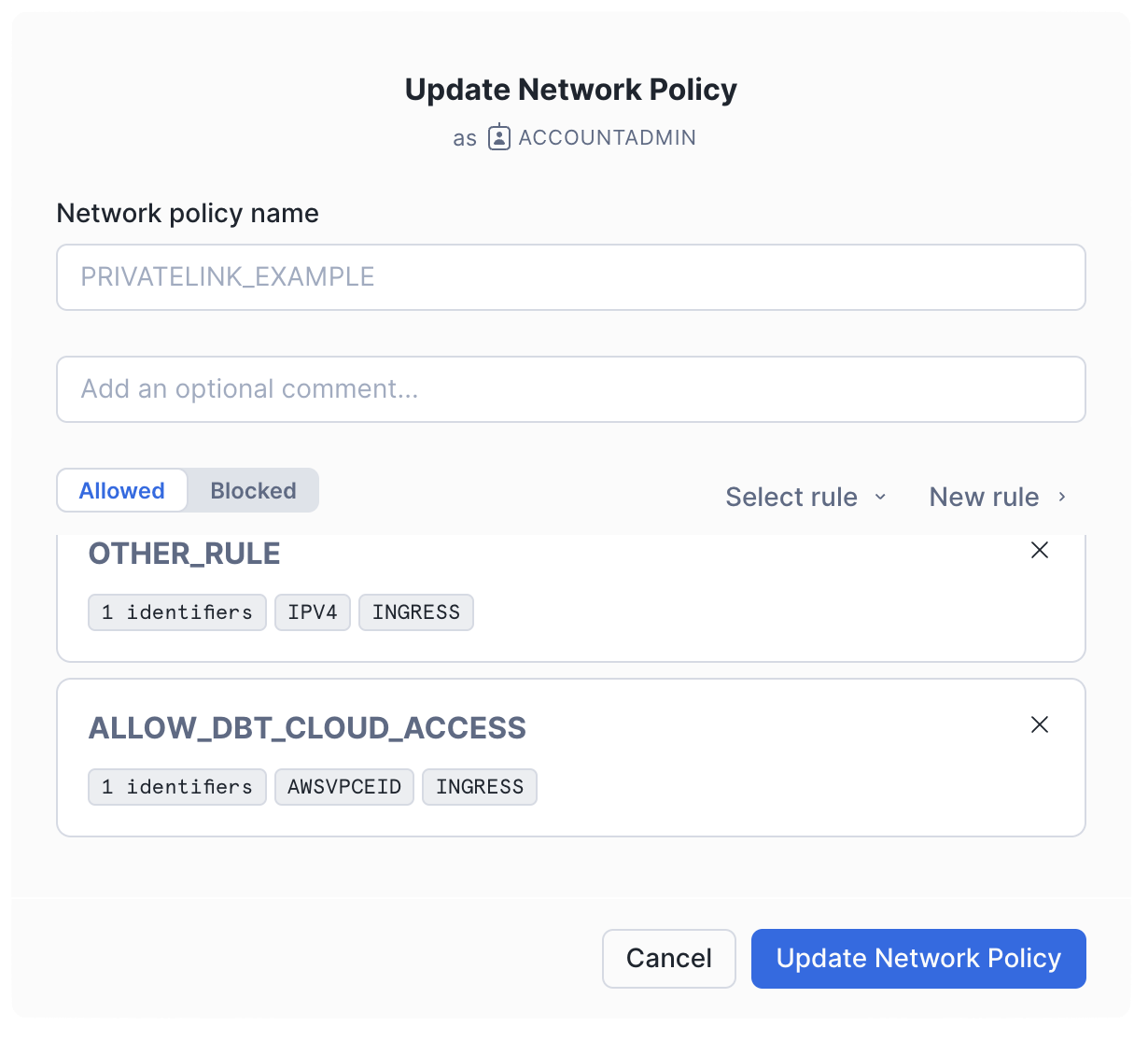
In the Network Policy tab, edit the policy you want to add the rule to. This could be your account-level policy or a policy specific to the users connecting from dbt Cloud.
-
Add the new rule to the allowed list and click Update Network Policy.
Using SQL
For quick and automated setup of network rules via SQL in Snowflake, the following commands allow you to create and configure access rules for dbt Cloud. These SQL examples demonstrate how to add a network rule and update your network policy accordingly.
- Create a new network rule with the following SQL:
CREATE NETWORK RULE allow_dbt_cloud_access
MODE = INGRESS
TYPE = AWSVPCEID
VALUE_LIST = ('<VPCE_ID>'); -- Replace '<VPCE_ID>' with the actual ID provided
- Add the rule to a network policy with the following SQL:
ALTER NETWORK POLICY <network_policy_name>
ADD ALLOWED_NETWORK_RULE_LIST =('allow_dbt_cloud_access');